Over the weekend reports started emerging about a new type of malware known as Silver Sparrow on macOS which was first discovered by the Red Canary security researchers.
Contrary to some reports, it not only affects new M1 Macs but also Intel Macs which are the vast majority of Macs out there.
Whenever a new piece of malware is discovered on Mac, there’s often a lot of hysteria and confusion over exactly how dangerous it is and what it does.
Many malware detectors such as MalwareBytes for Mac have now been updated to remove Silver Sparrow from your Mac.
You May Also Like:
Here we’ve taken a closer look at the myths and realities of Silver Sparrow on Mac and what you should know.
Table of Contents
Which Macs Does Silver Sparrow infect?
Silver Sparrow was initially discovered on the new Apple Silicon Macs with M1 chips but it’s also been found on Intel Macs.
You can check which Mac you have by going to the Apple logo in the top left of your desktop and selecting “About This Mac”.
How Does Silver Sparrow Infect a Mac?
At the moment the origins are not fully known but it appears to be an install file that is masquerading as an update to macOS.
It’s understood that it uses JavaScript to execute which hasn’t been seen before in any malware that’s detected on Macs.
Apple has already removed the binaries and revoked the certificates of developer accounts that were used to sign the packages that allowed Silver Sparrow to install on a Mac.
So there’s no way you can infect your Mac with Silver Sparrow anymore by anything downloaded from the Mac App Store.
What Does Silver Sparrow do?
It’s understood that the Silver Sparrow malware leverages the macOS Installer JavaScript API to execute suspicious commands.
So far it is understood to have infected around 30,000 Macs in around 150 different countries and is using Amazon Web Services plus Akamai to spread.
It seems that Silver Sparrow communicates with these services to check for commands to carry out in macOS but so far no commands have been issued.
At the moment, when executed on Intel Macs, Silver Sparrow simply displays a simple “Hello World!” message:
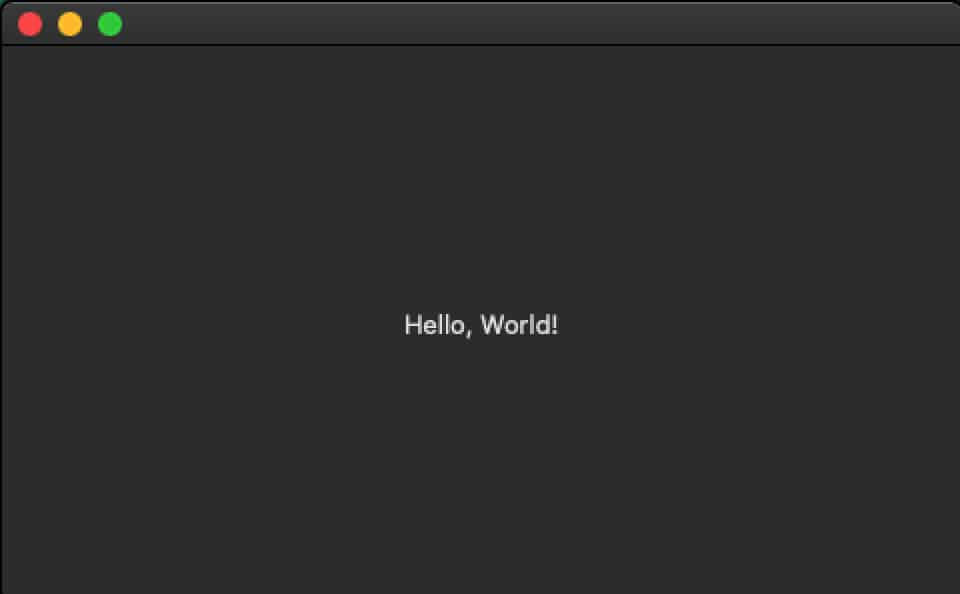
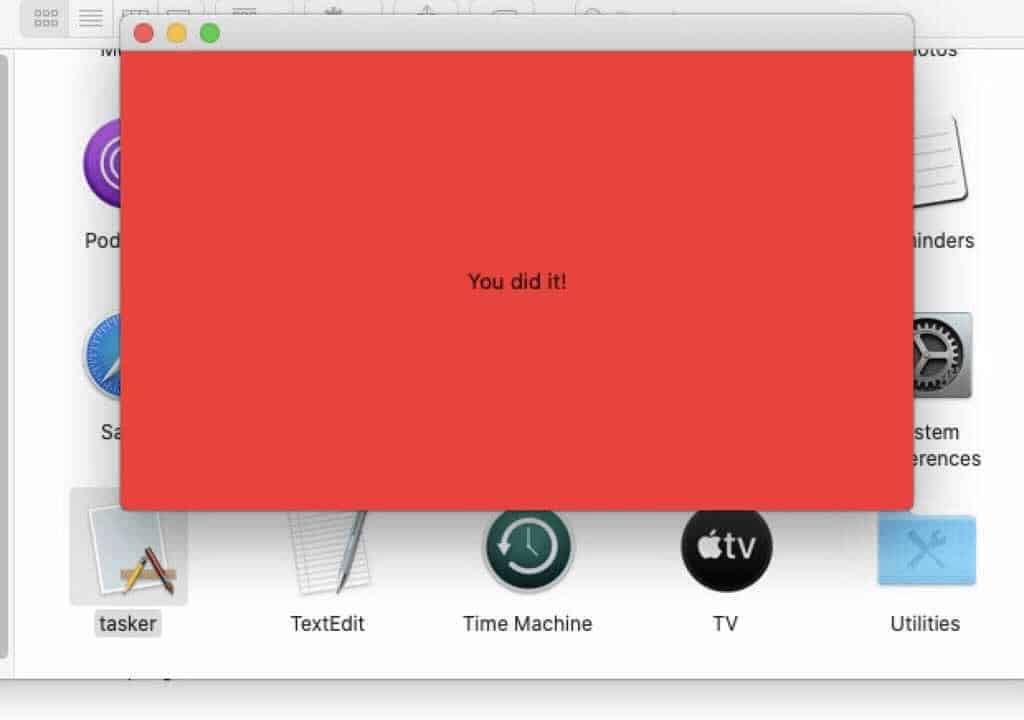
On M1 Macs, the same message reads “You did it!” in a red background:
How Harmful Is It?
As yet, there’s no evidence that Silver Sparrow is harmful to your Mac or data other than displaying the annoying messages above.
There has been no detected “payload” or malicious intent discovered so far so it’s purpose is something of a mystery.
How Do I Detect Silver Sparrow?
At the moment, anti-malware providers are rapidly updating their software to detect Silver Sparrow on Mac.
The best chance of detecting it on macOS is to use MalwareBytes for Mac which has now been updated to detect and remove it.
According to the Red Canary report that first discovered Silver Sparrow, the only way to detect Silver Sparrow on your Mac at the moment it to check for the following files on your Mac:
Malware Version 1
File name: updater.pkg (installer package for v1)
MD5: 30c9bc7d40454e501c358f77449071aaFile name: updater (bystander Mach-O Intel binary in v1 package)
MD5: c668003c9c5b1689ba47a431512b03ccmobiletraits.s3.amazonaws[.]com (S3 bucket holding version.json for v1)
~/Library/Application Support/agent_updater/agent.sh (v1 script that executes every hour)
/tmp/agent (file containing final v1 payload if distributed)
~/Library/Launchagents/agent.plist (v1 persistence mechanism)
~/Library/Launchagents/init_agent.plist (v1 persistence mechanism)
Developer ID Saotia Seay (5834W6MYX3) – v1 bystander binary signature revoked by AppleMalware Version 2
File name: update.pkg (installer package for v2)
MD5: fdd6fb2b1dfe07b0e57d4cbfef9c8149tasker.app/Contents/MacOS/tasker (bystander Mach-O Intel & M1 binary in v2)
MD5: b370191228fef82635e39a137be470afspecialattributes.s3.amazonaws[.]com (S3 bucket holding version.json for v2)
~/Library/Application Support/verx_updater/verx.sh (v2 script that executes every hour)
/tmp/verx (file containing final v2 payload if distributed)
~/Library/Launchagents/verx.plist (v2 persistence mechanism)
~/Library/Launchagents/init_verx.plist (v2 persistence mechanism)
Developer ID Julie Willey (MSZ3ZH74RK) – v2 bystander binary signature revoked by Apple
How Do I Remove Silver Sparrow?
If you can find the files referenced above, then you can manually delete them yourself.
We recommend using MalwareBytes For Mac too as it’s usually the first to be updated to remove new malware threats on macOS.
Be very careful about installing any other software which claims to “remove Silver Sparrow on Mac” as many of them are malicious programs which can’t do what they claim to.
Where Can I Find More Information on Silver Sparrow?
Silver Sparrow was initially discovered by engineers at Red Canary. If you want the full lowdown on what they found, you can find it here although it’s very technical and not readable for the average users.
If you found this useful, you may also want to check out our full review of Malwarebytes for Mac.
You can also read more on Apple’s decision to switch from Intel to Apple Silicon M1 chips here.


